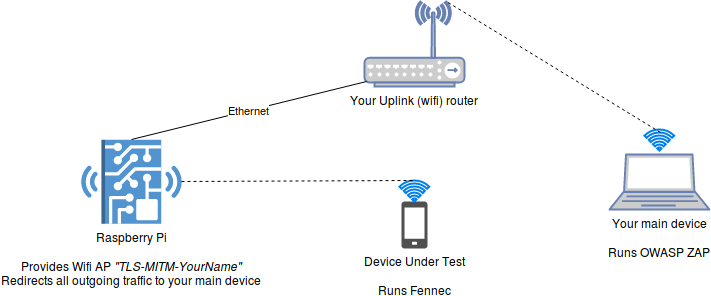
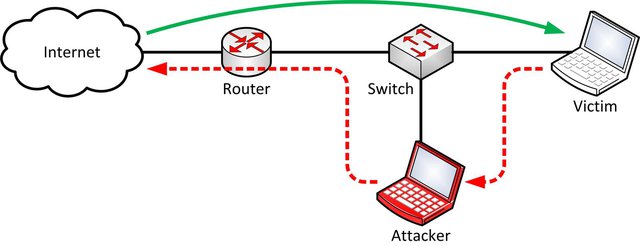
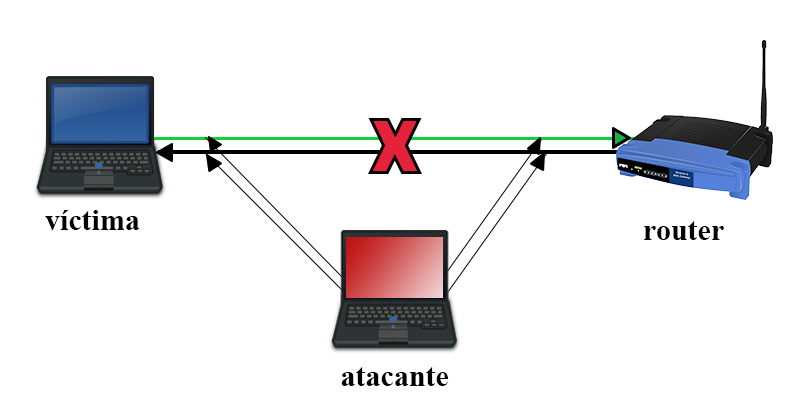
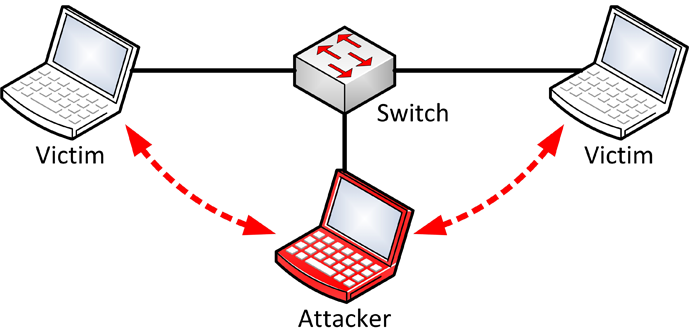
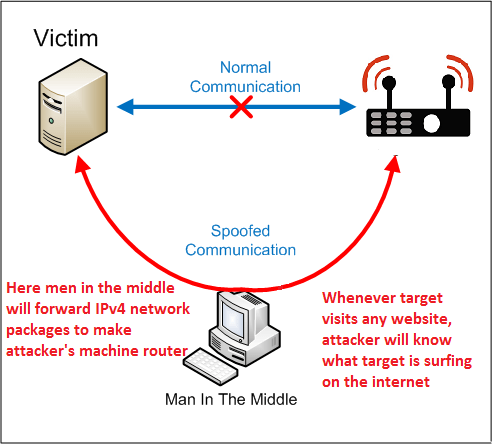
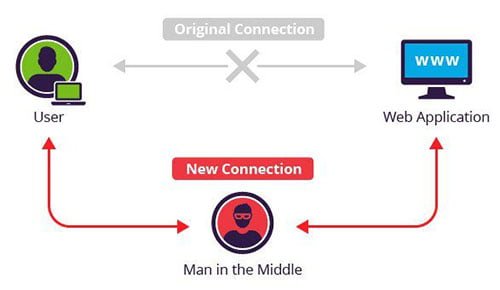
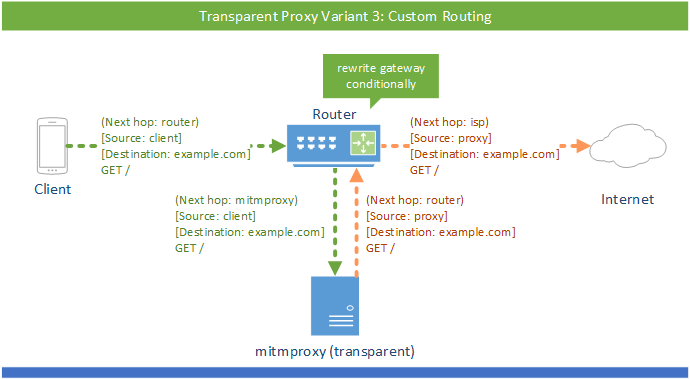
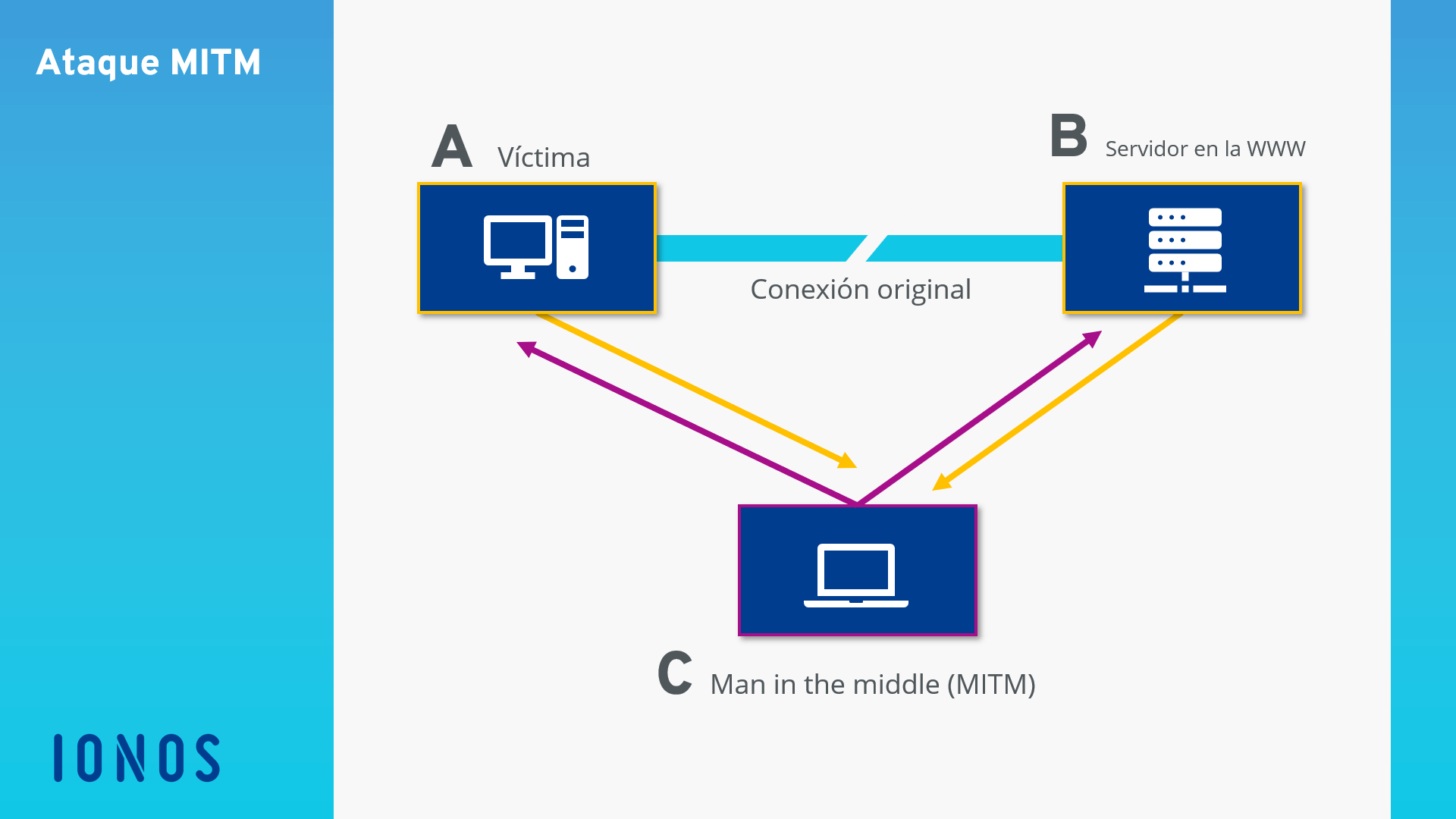
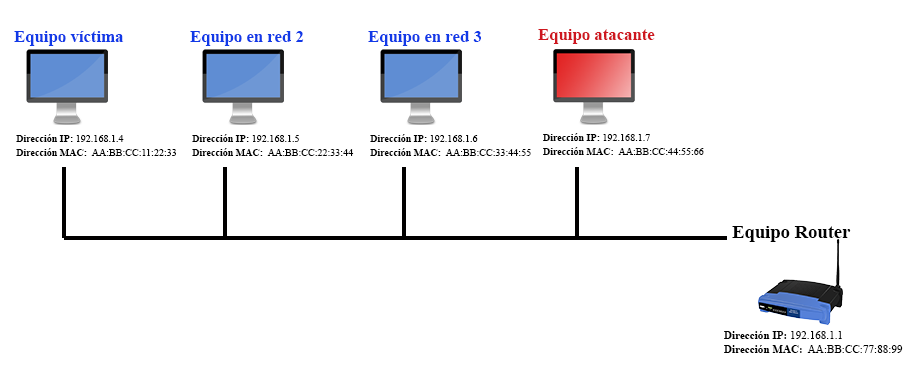
Timing diagram for address resolution protocol cache poisoning of the... | Download Scientific Diagram

Newly discovered 'Cable Haunt' flaw exposes nearly 200 million Broadcom-based modem cables to MITM attacks | Cyware Alerts - Hacker News
GitHub - brannondorsey/mitm-router: ☠ Man-in-the-middle wireless access point inside a docker container 🐳